Setting up Active Directory integration (NTLM)
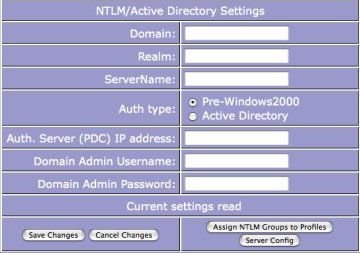
The following details are required to allow the Protex server to connect to the AD domain. When setting up NTLM authentication for Protex it is essential that the CacheBox's own NTLM mechanism is Disabled. Once all the required information has been entered the server will need to be rebooted. Once it has restarted log in again and go to Server Configuration -> Samba/NTLM status menu to confirm that Protex has joined your local domain.
- NOTE: Currently the ProtexLocal version on Appliansys CacheBox servers must be set up to use Pre-Windows2000 configuration without using a realm: for these servers the web interface does not present these*.
Browser Setting Requirements (for NTLM Authentication)
- must allow JavaScript
- must allow cookies
- "do not proxy for" setting must include the Protex server's FQDN and IP address.
- In almost all cases it is also preferable include the whole local network in the "do not proxy for" setting.
Domain
This is the Windows2000 compatible domain name and not a FQDN. Typically it will be a single string of UPPERCASE, e.g. MYSERVER.
Realm (ProtexLocalVA only)
This is the realm of you AD server. Typically it will be a single string of UPPERCASE characters formatted like a DNS domain with dots ('.'), e.g. MYSERVER.TEST. If you are unsure what to use contact your school Active Directory server administrator or network manager.
ServerName
The AD server's hostname - again this is not the FQDN.
Auth type
ProtexLocalVA: Depending upon the configuration on your server you can use either the Pre-Windows2000 or Active Directory (AD) authentication style. For newer Windows servers it is likely that the AD style with a realm will be required as it is more secure and connecting via the older RPC protocol is disabled by default.
ProtexLocal for Appliansys: You must use the Pre-Windows2000 authentication style. This may require some changes to the security settings on your Windows AD server as later versions (post Win2008) do not allow NTLMv1:
- Start the Security Policy Editor
- Go to: Local Policies > Security Options
- Find Network Security: LAN Manager - authentication level.
- Change the Setting from Send NTLMv2 response only to Send LM & NTLM -- use NTLMv2 session security if negotiated.
Auth. Server (PDC) IP Address
The IP address of the AD server or PDC.
Domain Admin Username
The user entered here should not be the main domain administrator for security reasons. A better option is to create a dedicated Protex user and make it a member of the Domain Administrators group.
If you want to restrict it further by creating a special group for the user with more limited rights then the essential abilities required of this user are:
- to be able to add machine accounts to the domain
- to be able to enumerate all the AD groups
- to be able to enumerate all the AD users
As individual AD configurations differ we do not support this last option - please feel free to experiment but we cannot support/troubleshoot connection problems where the connecting user is not a member of the Domain Admins group.
Domain Admin Password
The password of the user entered above.